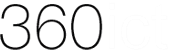Do you know the value of effective cybersecurity?
Protection for your hard work – your business, your sales, your data, your reputation.
Every day thousands of UK firms suffer cyber-attacks. From malware, to phishing to payment scams, cybercrime is costing small firms billions of pounds a year.
Nobody imagines it will happen to them.
The truth is that cybercriminals know many businesses are not sufficiently protected.
Hardly a day passes without news of another firm being hit by a cyber-crime or data breach.
Businesses should take action NOW.
360ict specialises in providing cybersecurity to the UK’s small businesses
Minimise the risk of loss of money
Prevent disruption to your business
Guard against damage to your brand reputation
Save on time, money and headaches
To protect your business get in touch using the phone number or form below;
|
Our security engineers are certified with: Offensive Security Certified Professional (OSCP) GIAC Web Application Penetration Tester (GWAPT) Certified Ethical Hacker (CEH) Certified Information Security Manager (CISM).
Penetration Testing (starting package, two man-days)
Black-Box Pentest – Web and Network Pentesting – Attacks without authentication
- 20 % automated tools , 80 % manual investigation and exploitation
- Discovery of sensitive public information about the system
- SQL Injection in authentication mechanism
- Direct pages access without authentication
- Webserver sensitive files access ? Brute-force
- Admin account discovery and brute-force
- Server side exploitation: services exploits, misconfigurations, brute-force
- Business logic: reset password of other users, user enumeration
- Public exploits
- User registration process
- and many more. White-Box -Web and Network Pentesting
- Authorisation checks
- Unauthenticated users accessing and altering resources of simple and admin users
- Simple users accessing and altering resources of admin users
- Users accessing resources of other users ( Horizontal attacks)
- Path traversal: accessing server files in browser
- Privilege escalation
- Users provisioning for themselves admin permission
- Local privilege escalation on server side: from local to root
- Technology specific vulnerabilities
- Programming language vulnerabilities
- Framework vulnerabilities
- Web server
- Depending on technology type discovered, public vulnerabilities for that technologies are tested
- Web Application & Server specific vulnerabilities
- Injection Attacks: SQL injection, XSS, HTML, XXE, Code injection, Buffer Overflow, Server side command injection
- Client Side: Open redirects, ClickJacking, CSS injection, Local storage
- SSL test: weak ciphers usage, sensitive information sent unencrypted, SSL vulnerabilities: Sweet32, BEAST, Padding and others.
- Business logic: payments, password change, application misuse scenarios, request forgery, hidden content, process timing (race condition)
- File upload: malicious file upload, unexpected file upload, server side control using ASP webshells
- Web Server configuration: error codes, stack traces with sensitive information, HTTP splitting, config files exposure
Cyber Security Program Development (long term planning and strategy)
A long term plan to develop the security posture of a company, based on the capability Maturity Model. At the end of this period the client will have confidence that his Risk Profile reaches the desired level.
- on-site and off-site meetings with Consultant
- complete Program Plan, with all the implied projects
- coaching throughout the implementation Subjects Covered:
- Security Basics: Social Engineering, Physical security, Desktop security, Wireless networks, Password security, Malware
- Risk Management and Compliance (Risk Catalog; definition of desired certification for example ISO 27001, PCI-DSS, etc.; local and international laws)
- Roles and Responsibilities (CSO; CISO; CEO)
- IT Security Governance (Risk Profile; Industry requirements)
- IT Security Process and Program Management (yearly plan: awareness training, penetration testing, audits)
- Defining and Monitoring the Security Posture (KPIs)